▬ RF-Centric Machine Learning
Mobile technologies, fueled by advances in wireless communications, revolutionized our society beyond the pioneers' dreams. It enables ubiquitous access to information, and connects people to each other, and to a rapidly increasing number of services, and businesses. However, a plethora of emerging applications, such as Massive IoT (MToT), autonomous cars, robotics, and augmented reality are driving the demand for spectrum to new heights. Spectrum scarcity is becoming a critical issue. At the same time, wireless systems are increasingly softwarized, and SDR platforms are highly capable, with small form factor and low cost. This is both a blessing for developing new communications techniques, and a curse as it lowered the barrier for attacks from smart jamming, to tracking, spoofing, compromising wireless chips, or weaponizing drones. On the other hand, advances in machine learning and its success in computer vision demonstrate what can be achieved when adequate deep learning models leverage large datasets and computation power.
This confluence of trends raises challenging research questions to: understand the spectrum, in real-time and a-posteriori, detect, classify, and predict communication patterns in time, frequency, and space in order to fine-grain share the spectrum efficiently as well as to mitigate unintentional and malicious interference, or threats from drones. Agencies such as the FAA and FCC have regulations against such threats, but not the necessary technology to enforce them. Our approach is multi-fold, capitalizing on the advances in ML, and the flexibility and computational capability of SDRs, while addressing, from the ground up, the need to understand and adapt in real-time in a crowded spectrum and the presence of malicious actors. In particular, we seek to devise RF-Centric machine learning techniques to address these challenges, including the development of new RF-Centric ML model architectures, feature extraction layers, activation and regularization functions.
DARPA Spectrum Collaboration Challenge (SC2): Our initial results where demonstrated within the DARPA Spectrum Collaboration Challenge (SC2) where our team Sprite representing Northeastern University (led by Guevara Noubir, and Triet Vo-Huu and included doctoral students Tien Vo-Huu, Hai Nguyen, Norbert Ludant, and Marinos Vomvas) was a winner in the 2017 Preliminary Event 1 ($750K), and a winner in the 2018 Preliminary Event 2 ($750K), and a finalist in 2019. Besides the development of novel elastic Pilotless Filter Bank Multicarrier communications techniques, we demonstrated the ability RFML technique to detect, classify, and localize in time and spectrum emissions from a variety of communication technologies.
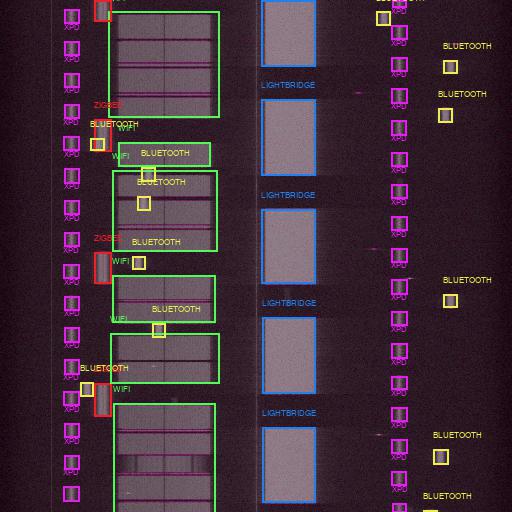
Detecting, Localizing and Classifying Arbitrary Emissions: We later extended our techniques developing a framework for systematic and generalizable detection and classification of RF emissions with the ability to operate in real-time, over a wideband spectrum, and even in highly congested environments. We applied our approach to commercial waveforms including Wi-Fi, Bluetooth, ZigBee, Lightbridge (DJI drones) and XPD (microphones), achieving over 95 mean Average Precision (mAP) processing over 6Gbps streams of RF samples corresponding to 100MHz [SC2-RFML].

▬ Cellular Systems Security and Privacy: 5G and Beyond
The 3GPP 5G cellular system is hailed as a major step towards a ubiquitous and pervasive communications infrastructure. It is indeed flexible and extensible, with slices to support a variety of unique applications requirements, from Massive IoT (MIoT), Ultra-Reliable Low-Latency Communications (URLLC), to enhanced Mobile Broadband (eMBB), and massive Machine Type Communications (mMTC), as well as specific industry requirements such as V2X, Smart Grid, and Remote Healthcare. This capability to address unique needs, along with the redesign around Service Based Architecture, and Network Functions Virtualization is very promising to adequately support a larger number of applications including critical ones such as self-driving cars, robotics, and remote surgeries.
Cellular systems, however, have a history of security, privacy, and robustness issues since their second generation (GSM) that took security and privacy more seriously. Over the years, we and other researchers around the world were able to demonstrate attacks against every generation of cellular systems from 2G to 4G, by preying on design, implementation, and operation flaws. Within projects funded and in collaboration with the DoD we have been analyzing the security, robustness, privacy of 5G systems and devising protections for current and future generations of cellular communications systems. Our research runs along three main axes: (1) analysis of security and privacy threats, (2) design and implementation of countermeasures, and (3) testbed setup and experimental validations. We identified several vulnerabilities in the 5G design pertaining to both DoD networks and general networks (e.g., the ability to stealthily spoof the 5G signal synchronization block with emissions 3.4dB below the legitimate signal). We developed several mitigations, implemented them, and evaluated them in our testbed using the 5G Open Air Interface platform. We are interested in the security of both Radio Access Network (RAN) and the Core Network.
▬ IoT Security and Privacy
Bluetooth (Classic and Low Energy) Privacy Leaks. Our analysis of the widely used Bluetooth Classic, demonstrates that it is possible to extract the devices' unique address in real-time and from a distance, even when such devices are idle. It was also believed that a careful use of MAC address randomization prevents the tracking of Bluetooth Low Energy (BLE). We demonstrated that this is not the case exploiting a side-channel linking the clock of BLE and BT Classic. This had the implications that the vast majority of BLE-based privacy-preserving mobile apps do not meet their claimed security guarantees. While fulling defending against these attacks requires a redesign of Bluetooth Classic, and/or BLE chipsets, we developed several short term mitigations for the Android phones.
Wi-Fi Security. We demonstrated that it is possible to fingerprint Wi-Fi network interfaces, exploiting leakage from RF emissions at the physical layer. Such attacks leverage the statistical distributions of RF transients, Carrier and Sampling Frequency Offset, and scrambling seeds.
Embedded Systems Security. We demonstrate that several IoT devices despite the use of Trusted Execution Environments (such as ARM Trustzone) remain vulnerable to attacks. For instance, we developed a set of IoT forensics techniques, and applied them to reverse engineer the hardware and software of the Amazon Echo Dot and other smart speakers. We demonstrated their lack of adequate protections of private user data. An adversary with physical access to such devices (e.g., purchasing a used one) can retrieve sensitive information such as Wi-Fi credentials, the physical location of (previous) owners, and cyber-physical devices (e.g., cameras, door locks). We show that such information, including all previous passwords and tokens, remains on the flash memory, even after a factory reset. This is due to the wear-leveling algorithms of the flash memory and lack of encryption. We identify and discuss the design flaws in the storage of sensitive information and the process of de-provisioning used devices. We demonstrate the practical feasibility of such attacks on 86 used devices. We also proposed secure design alternatives and mitigation techniques.
Mobile Privacy: the MATRIX System. In previous research we demonstrated that it is possible for a malicious mobile app to infer private information about a user, including location, travelled trajectories, and even key presses. Such attacks do not require user permissions as they exploit zero-permissions sensors (Accelerometers, Gyroscopes, Magnetometer). We designed, implemented and evaluated a system, called MATRIX, to protect the privacy of users of mobile device against location inference and sensor side-channel attacks. MATRIX gives users control and visibility over location and sensor (e.g., Accelerometers and Gyroscopes) accesses by mobile apps. It implements a PrivoScope service that audits all location and sensor accesses by apps on the device and generates real-time notifications and graphs for visualizing these accesses; and a Synthetic Location service to enable users to provide obfuscated or synthetic location trajectories or sensor traces to apps they find useful, but do not trust with their private information.