Cryptography Laboratory
November 1997
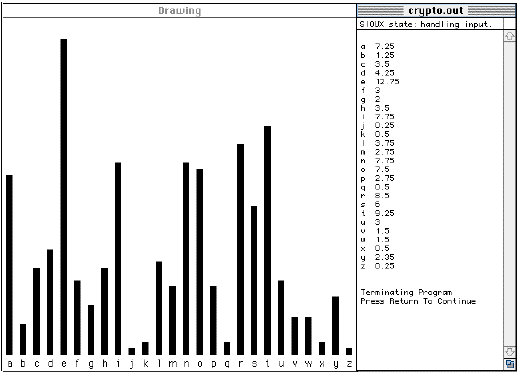
The bar chart below is a representation of the data shown in the crypto.out window.
These are the frequencies of letters in common English text expressed as percentages.
The bars have been scaled to fit the window.
These are percentages
Julius Caesar used a cipher that moved each letter to the letter three to the right:
A -> D B -> E C -> F and so on.
Any cipher which moves the ith letter to the (i+j)th letter is called a Caesar Cipher.
For example:
Message:
Never had we seen so many fireflies congregated on one spot; they flicked through
the trees in swarms, they crawled on the grass, the bushes and the olive trunks,
they drifted in swarms over our heads and landed on the rugs like green embers.
Glittering streams of them flew out over the bay, swirling over the water, and then, right on
cue, the porpoises appeared...
Encryption:
ulcly ohkdl zlluz vthuf mpylm splzj vunyl nhalk vuvul zwvaa olfms pjrlk
aoyvb noaol ayllz puzdh ytzao lfjyh dslkv uaoln yhzza olibz olzhu kaolv
spcla yburz aolfk ypmal kpuzd hytzv clyvb yolhk zhuks huklk vuaol ybnzs
prlny llult ilyzn spaal ypunz aylht zvmao ltmsl dvbav clyao lihfz dpysp
unvcl yaold halyh ukaol uypno avujb laolw vywvp zlzhw wlhyl k
Here A -> H B -> I C -> J D -> K E -> L etc.
In the encrypted message, spaces and punctuation are ignored and the letters are set
in groups of five to make it harder to decipher.
In the folder "messages " you will find ten folders, each containing three messages,
similarly encrypted but with different shifts. The encrypted message 'fireflies.crypt'
shown above is also there.
o 0.
The message folders are named "messages0" through "messages9".
You must decrypt the messages in the folder ending with the same MIDDLE digit as your
student ID number.
o 1.
Write a program that reads an encrypted message file, computes the frequency (number
of occurrences of percentage) of each character and draws a bar graph similar to
the one above. The encrypted message above has the bar chart shown on the next page.
o 2.
Run your program for each of your three encrypted messages. Print a picture of the frequency bar chart
for each message. Label the graphs so you know which one goes with each message.
These are number of occurrences.
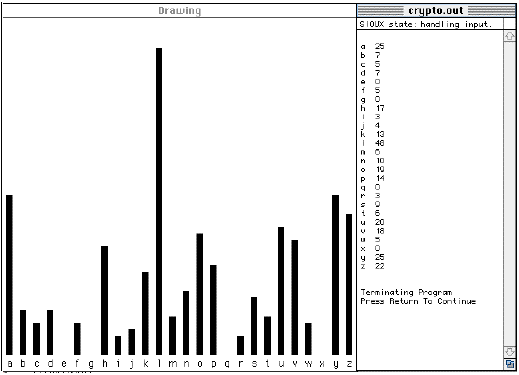
Comparing this bar chart with the one for English, we see that 'E F G' in this graph
are a good match for "X Y Z' in the English graph. That is, Z -> G, A -> H and so
on. That is, in fact, the cipher that was used.
o 3.
Compare your bar charts with the English one and deduce the shift that was used to
encrypt the message and write
this, neatly, on the page with the printed bar chart.
o 4.
Write a second program that:
a.
Inputs a text file.
b.
Prompts the user for a shift
(0 <= shift<=25)
c.
Writes a new text file that is the old file shifted.
o 5.
Use your second program and the shifts you found in part 3 to decrypt your three messages.
For each decrypted file, do the following:
a.
Open the file in teachtext
b.
Adjust the first line to correct the word boundaries. See the example in the box
below. Put the encrypted file name at the top, e.g. c16.
f.crypt
never had we seen so many fireflies congregated on one spot they flicked
throu ghthe trees inswa rmsth eycra wledo ntheg rasst hebus hesan dtheo
livet runks theyd rifte dinsw armso verou rhead sandl anded onthe rugsl
ikegr eenem bersg litte rings tream softh emfle wouto verth ebays wirli
ngove rthew atera ndthe nrigh toncu ethep orpoi sesap peare d
o 6.
Print out your three decrypted files.
Turn in:
o A diskette with your two programs, each in its own project, ready to run.
o Your labeled printouts of the three frequency graphs, showing the shift you deduced
in each case.
o The printouts of your three decrypted files.
Due:
at your class on Thursday November, 20, 1997
Hints:
o 1.
Use an array to count the occurrences of each letter.
typedef FreqArray = int[26];
FreqArray A; // Remember to set all the values A[k] to 0.
When you read a character that is between 'a' and 'z', update its frequency.
if (('a' <= ch) && (ch <= 'z'))
A[ch - 'a'] += 1;
To find percentages of each letter in the text, compute the total
number of letters in the message as you read it or by adding up the frequencies.
Divide the number of occurences of a letter by the total to get the percentage.
o 4.
Remember that if 'a' --> 'g' to encrypt, then 'g' --> 'a' to decrypt.
A Template for Reading, Transforming, and Writing:
The following code outlines the process of opening one file for reading and another
for writing. The data is read from InFile, transformed, then written to OutFile.
// Get name of old (encrypted) file
if (SelectOldFileName(InFileName) // InFileName is of type string
// get file name of new file
if (SelectNewFileName(OutFileName)
if (OpenFile(InFile, InFileName, textread)
if (OpenFile(OutFile, OutFileName, textwrite) {
while (InFile.get(ch)) {
transform the data item, ch
send zero, one, or more new items of data to OutFile
}
{ close both files }
InFile.close();
OutFile.close();
}
Notice that this code asks the user for the name of the old file, then if the user
has not clicked CANCEL this code asks for the name of the new file, then if the user
has not clicked CANCEL the work on the two files begins.
Last Updated: November 16, 1997 11:39 am by
Harriet Fell
College of Computer Science, Northeastern University
360 Huntington Avenue #161CN,
Boston, MA 02115
Internet: fell@ccs.neu.edu
Phone: (617) 373-2198 / Fax: (617) 373-5121
The URL for this document is:
http://www.ccs.neu.edu/home/fell/COM1100/HW/Crypto.html

